
Personally identifiable information has been called “the new oil.” This data is the touchstone of the modern world, required for everything from opening a bank account to participating in social media. It’s also the most sought-after data type in cyber attacks. So how can organizations successfully protect that information while complying with ever-expanding privacy laws?
Information security standards: ISO 27001
The International Organization for Standardization (ISO) is one of the best-known names in international standardization, recognized in over 160 countries worldwide. The ISO 27001 certification, which requires both a documented information security management system and an external annual audit, is one of their most popular offerings.
Because ISO standards are accepted so widely, they must ensure compliance with a range of national and international laws and requirements. This broad applicability can result in frustration for people involved in implementing the ISO 27001 standard, who sometimes want specific, technical guidance.
To take a specific example, Annex Control 8.1.3 requires that “Rules for the acceptable use of information and of assets associated with information and information processing facilities shall be identified, documented and implemented.”
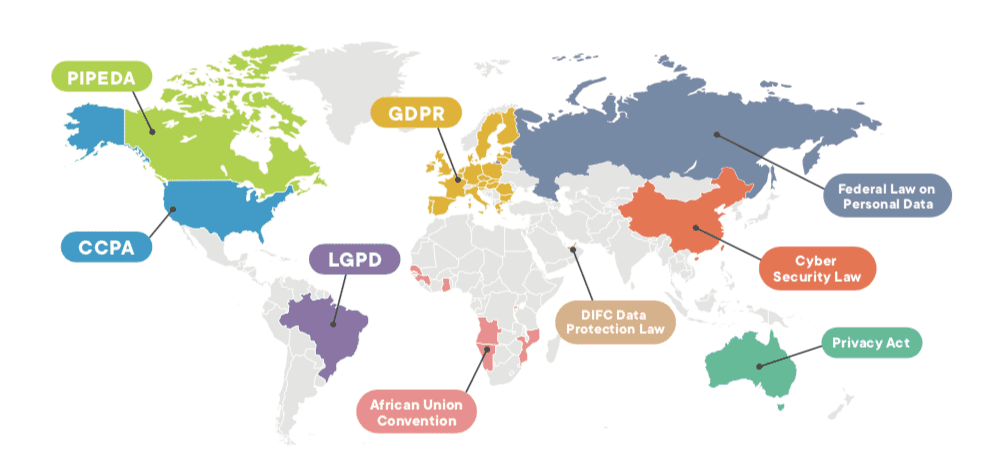
If you’re in France, those rules are going to look very different from those in force in China, and the requirements for China are going to look different again to those applicable in Canada.
Legislative parallels
Privacy laws and regulations undergo lengthy review and approval processes before publication, and therefore avoid technical specifics so they aren’t outdated by the time they’re enforced. Similarly, the ISO 27001 standard states high-level requirements, and relies on the willingness and the competence of individual organizations to do the necessary research to ascertain how best to comply. For example:
- The European GDPR, as one of the benchmark pieces of privacy legislation to date, has similarly high-level aims: “Personal data shall be … processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures…”
- Alternatively, there’s the Californian CCPA: “…duty to implement and maintain reasonable security procedures and practices appropriate to the nature of the information to protect the personal information…”
- We can also look to PIPEDA in Canada, which requires that “Personal information shall be protected by security safeguards appropriate to the sensitivity of the information.”
When it comes to reviewing applicable law for Annex Control 18.1 (Legal and contractual compliance), it quickly becomes apparent that while awareness of the legislation is key — and in some cases, regulation can clarify requirements or add specifics — achieving compliance requires more than a checkbox exercise.
Supplementing ISO 27001
Organizations looking to implement information security aligned with legislation or ISO 27001 need a project lead who is capable of identifying what rules apply, who has the technical writing skills to convey the requirements clearly, and who has sufficient authority to implement them consistently.
It also means, particularly where a company will be handling sensitive information, that compliance can’t just stop at the level of “encryption, there should be some,” but instead needs to be supplemented with specifics.
Luckily, there are a number of technical frameworks and best practices that can be referenced to provide a solid foundation for ISO 27001 compliance.
NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST), is a U.S. government institution that was tasked with developing voluntary guidance to manage and reduce cybersecurity risk.
The framework was published in 2014 and updated in 2018, and is slightly more granular than the ISO 27001 standard. It is U.S.-centric, but provides a solid set of cybersecurity requirements, where the categories under each function supply high-level aims, and the subcategories add more specific requirements.
To compare the two, the ISO 27001 objective under “responsibility for assets” is “to identify organizational assets and define appropriate protection responsibilities.”
That breaks down into:
- An inventory of assets (assets and facilities associated with information processing shall be identified and inventoried)
- Defining who owns identified assets
- Documenting and implementing rules for the use of identified assets
- A requirement for users to return organizational assets on termination of employment/contract
The equivalent section in NIST Cybersecurity for asset management (ID.AM) requires that organizations:
- Specify assets (physical devices and systems, software platforms and applications)
- Map organizational communication and data flows
- Catalog external information systems
- Prioritize resources based on classification, criticality and business value
- Establish cybersecurity roles and responsibilities for the entire workforce and third parties
Both these sections have the same basic goal, but NIST provides some additional topics that flesh out the ISO requirements while working through ISO 27001 certification.
Other frameworks that can be referenced while working through ISO 27001 are SOC 2 Type 2 criteria, or COBIT.
According to the Australian Compliance Council:
Businesses shouldn’t normally need to choose between the two frameworks or find them contradictory. Both allow a lot of flexibility for the specifics of achieving the required goals rather than prescribing specific measures.
As well as having different scopes, the two frameworks will normally have their biggest effect on different layers of an organization’s hierarchy. ISO 27001 covers a narrower, more specific area that’s usually the realm of mid-level staff. COBIT covers a broader area that’s more likely to involve decisions by top-level staff.
OWASP guidance
The Open Web Application Security Project® (OWASP) is a non-profit group that aims to improve software security and offers a range of open-source tools and documentation.
Although ISO 27001 covers the need to address securing application services in Annex Control 14, OWASP’s guidance can flesh out how to meet those requirements, particularly where a company develops its own software.
A good example is the OWASP Top Ten, which is a list of the most critical security risks to web applications. Incorporating steps to minimize these risks in complying with Annex Control 14.1 is a solid step towards operationalizing compliance.
Another OWASP offering to consider is the Application Security Verification Standard. While this document will support compliance with Annex Control 14, there is also broad applicability in Annex Control 8 (Asset Management), Annex Control 9 (Access Control), Annex Control 12 (Operations Security), and Annex Control 18 (Compliance).
ISO 27001 is about more than checkboxes
The ISO 27001 is not a standard conducive to “checkbox compliance,” or in other words, doing the bare minimum to meet the letter of the requirements. This standard is an excellent litmus test for how a given company views their information security. When efforts to ensure best practices are incorporated across all 114 controls, and a comprehensive suite of policies and procedures is in place and adhered to, it’s a very positive sign for the company’s information security and culture of compliance.
In contrast, checkbox compliance has the potential to leave gaping holes in an organization’s information security, with potential negative impacts on reputation, consumer trust, and continued operations.
Commitment to end-to-end compliance, transparency, and information security is increasingly vital in a world where large-scale data breaches are becoming commonplace and the infrastructure is increasingly complex. More than ever before, information security is a team sport: the days of a small IT team locked in a dark room with an industrial-sized coffee-maker are gone. The “human firewall” is an incalculable asset, and, like any good wall, it doesn’t function nearly as well if there are gaps.
Solutions
Trust and Safety
Reinforce Customer Trust With Secure, Compliant Onboarding
Resources Library

Trust and Safety
Executive Summaries
Building a safer marketplace
Featured Blog Posts
Business Verification (KYB)
Enhanced Due Diligence Procedures for High-Risk CustomersIdentity Verification
Proof of Address — Quickly and Accurately Verify AddressesBusiness Verification (KYB)
How to Verify Legitimate Businesses and Merchants

