Social media is full of trolls, bots, cyberbullying and fake news. While some of it we can laugh off, unfortunately, there are troubling real-world consequences. Social media affects politics, interactions and what we believe as people and society, resulting in conspiracy theories and abuse.
How can we better manage social media without censorship? How can we enable people to interact, discuss and learn globally without limiting free speech? How can we empower true expression without fear of retribution?
There’s a growing call for social media companies to require identity information to access their platforms. For example, there was a petition to make verified ID a requirement for opening a social media account in the UK. In Australia, they’re considering a social media ID requirement. A bill in the French Senate is looking to ban anonymous social media accounts.
While none of these have become law, it does raise the question of how best to handle identity when it comes to social media.
Anonymous vs. real names vs. authenticated names
Some social media encourage the use of real names. For example, Facebook and LinkedIn both have real name policies, as users often deal with people they already know. But identity verification isn’t a requirement for all users. There are use cases for identity verification for these platforms, such as participating in marketplaces or account retrieval, but in general you don’t need to verify yourself.
Other social media platforms thrive on anonymity. For example, Twitter and Reddit both have no requirement to use your real name but do have rules around impersonation and using names (or handles) that mislead or deceive.
A hybrid approach is emerging, where certain accounts are verified on anonymous platforms. An example of this is Twitter Verified accounts, “authentic, notable, and active” accounts of public interest. To get a blue Verified badge requires going through an identity verification process.
Anonymity vs Accountability
As witnessed by the fact that different social media platforms use differing name policies, there are advantages and issues with any current approach.
Anonymity, not tying the online persona to a real person, enables people to express things they might not want to say otherwise. A whistle-blower can call out injustice. Members of minority groups, or holders of unpopular opinions, can post and participate in communities with less threat. People’s comments are judged by their expressions, not their color, race, religion, sex, age or other factors potentially subject to discrimination.
But anonymity does not mean 100% anonymous. People are doxxed, where their real information is discovered and publicized. Governments can attempt to force social media platforms to provide data pinpointing a person. People hoping to be anonymous are putting their faith in the social media platform’s privacy policies and data security.
Anonymity can also enable inappropriate or hateful expressions that people might never do if publicly accountable for them. The speed, convenience and apparent lack of consequences can help foster hate speech, abuse, racism and other forms of anti-social discourse. A September 2020 survey found that 41% of Americans have personally experienced some form of online harassment, with about 75% of those saying the latest occurrence was on social media channels.
It’s difficult to pinpoint precisely how much anonymity contributes to the negativity that happens on social media because even social media platforms that have a real name policy also have issues with problematic discourse.

Better content tools and processes
One opportunity for the industry is the development of more sophisticated moderation tools. Using AI tools to analyze the vast amounts of posted content can enable better issue spotting and help identify potential problems. In general, they already have policies to block content or users and limit distribution, so refining and scaling moderation methods can help.
Some leading social media platforms and technology companies are working to create best practices for trust and safety that cover product development, governance, enforcement, improvement and transparency. The goal of these best practices is to help reduce the harms associated with online interactions while also protecting people’s ability to participate in the numerous opportunities the online world offers.
But perhaps there’s an opportunity to reexamine how we use identity online? After all, the lack of an identity layer on the internet is a key reason we’ve ended up where we are now. There’s no common, built-in mechanism to understand who is on the internet, so each company has to determine their strategy and processes for themselves. As a result, identity for social media is fragmented and the ensuing problems are difficult to solve together.
With initiatives to develop a fundamental identity layer under consideration, a more holistic solution might be possible and one outcome could be a model that integrates accountability and anonymity.
Unknown, known and verified identities
According to David Birch, an internationally-recognized thought leader in digital identity and digital money, “we can deliver verifiability in a privacy-enhancing manner.”
One problem with the current state of social media identity is that one identity attribute often links to numerous other identity attributes; sharing one piece of identity data can lead to a substantial identity profile. So, if a person provides a real name, quickly discovering their age, location, interests and numerous other data points are possible.
The person might not even be aware of all of that profiling, with the specific terms for use being buried deep in online contractual agreements hardly anyone reads. And for the social media platform, there’s a high cost and risk to gathering and storing this information – is it even needed?
Birch suggests that under this model people only provide the necessary identity attributes for a service, not access to a complete identity profile. For example, a service restricted to those who are 18+ doesn’t need a name or even a date of birth; they only need a verification of the identity attribute of being over 18.
The service uses digital identity technology to request an age verification (18+). The identity system knows the attribute from previous verifications and will provide the attribute (with permission.) No personal data is exchanged or needed.
The same model can work for social media platforms to block bots. With the model proposed by Birch, there would be three classifications of users: unknown, known and verified. To ensure an account is for a real person, they’d verify the IS_A_PERSON attribute. For example, using the digital identity system, the service would ask the person to allow their bank to confirm that they are a person. The bank gets the request, and as they have done their checks, they can verify IS_A_PERSON.
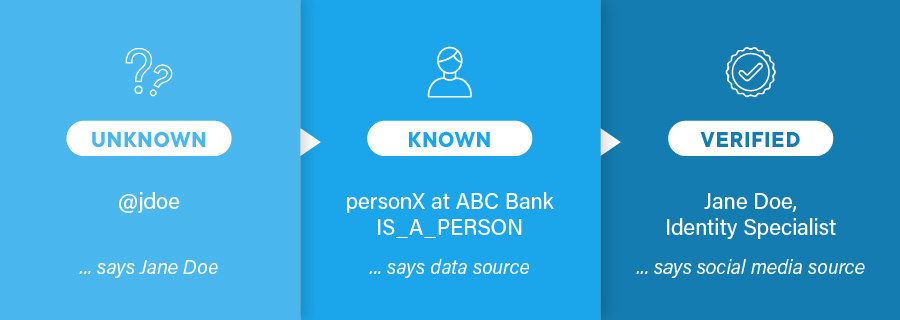
Credit for the concept: David Birch https://blog.dgwbirch.com/?p=562
The social media service can then set the account’s status to known. As with the age verification example, they don’t need the name to verify IS_A_PERSON. The person controls their information and can revoke or assign privileges as they see fit. The social media company can still operate similar to how they work now. Ad profiles can still be built up and optimized and even shared (with permission) but with no need for private information.
Of course, this digital identity system is still a work in progress. Creating the technology, developing business models and transforming well-entrenched processes is a massive task. But the opportunity is significant. As the Tony Blair Institute for Global Change suggests
To make progress, a secure, user-centric digital identity combined with new tools and features related to user verification could be a crucial part of the design of a well-functioning social network.
At Trulioo, we believe in the amazing opportunities of an intelligent, scalable and adaptable digital identity framework. We know that the next generation of identity systems need to balance different requirements, integrate different layers of identity to fit the use case and provide information on a need-to-know basis.
We genuinely believe there are ways to consider and optimize trust, privacy and inclusion. The need for trust should not overpower privacy or vice versa. With the right solutions, social media can offer freedom of speech and protect privacy for everyone.
Solutions
Individual Verification
Simplify KYC Identity Verification Across the Globe
Resources Library

Know Your Customer
White Papers
Build Trust and Safety With Digital KYC
Featured Blog Posts
Business Verification (KYB)
Enhanced Due Diligence Procedures for High-Risk CustomersIdentity Verification
Proof of Address — Quickly and Accurately Verify AddressesBusiness Verification (KYB)
How to Verify Legitimate Businesses and Merchants




